5 Major Types of Denial of Service Attacks & 7 Ways to Save Your Website from DOS & DDOS
Yahoo!, Buy.com and many other leading internet portals have come under Denial of Service attacks in recent times.
No matter how big an entity is, there is always the risk of a denial of service attack that can potentially crash the system worldwide. We have all heard or read about such malicious attacks on some of the biggest names in the world of internet. Even Wikileaks was not spared.
Although the damage is not permanent and websites recover from such attacks soon enough, the Denial of Service attacks do cause losses. While the perpetrators of such attacks may rejoice in having brought down the biggest names in the world for a few hours, millions of businesses depending on these sites stand the risk of incurring losses.
What is Denial of Service Attacks?
By definition, a Denial of Service attack exhausts the targeted system’s resources and bandwidth such that it becomes unable to process legitimate requests. To understand a Denial of Service attack, it is important to understand the how a server and client computer communicate.
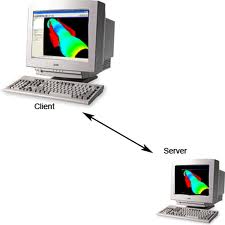
Let us take into consideration a typical connection between a client and server system.
- A client sends a request to the server and the server responds back with the data or information requested.
- As a typical example suppose you click on a link on a website. You are actually sending a request to the server to process your request, in this case a new link, and send the information that you requested, in this case, the webpage corresponding to the link that you clicked.
- Though you may see the requested webpage within a matter of seconds, there is a lot of processing that goes on behind the scene.
- Before you can actually receive the information, the client system sends a request for authentication to the server and receives an approval if the server accepts the request.
- The client system acknowledges the received approval before accessing the server for information.
Denial of Service Attack – Demystified
In a Denial of Service attack, a single client sends multiple authentication requests to the server with bogus return addresses. The server, which cannot determine if the addresses are false, tries to send a response back to these addresses.
As per the protocol, the server waits for a small amount of time to trace the client and finally closes the connection. When the client repeatedly sends false requests, the server keeps waiting and becomes engaged for an indefinite period of time.
During this time, other legitimate users will not be able to access the server and receive any response from the server as it is busy trying to process the false requests.
Types of Denial of Service Attacks
As the communication protocol between a client and a server has several layers, the attacks can target any part of the system. From resources to bandwidth, every part of the computer system is vulnerable to a Denial of Service attack. Experts have broadly classified the attacks as:
1) TCP SYN Flooding
In a TCP SYN flooding denial of service attack, all the system resources are consumed and no more new TCP connections are possible. Here, the attackers make use of the basic connection establishment process in TCP three-way handshaking protocol along with false IP addresses.
The attacking client station makes up a false address and sends a request to start establishing a connection to the server by sending a SYN message. The server responds with a SYN-ACK unaware that the address is a false one and waits for an ACK response which of course never comes.
The connection remains open partially in a wait state till it times out. Till that time, system resources are kept busy. Taking advantage of this, the attacker floods your server with connection requests or SYN packets all of them containing false addresses.
The server treats each one of them equally and waits for the last ACK for a period of time before timing out. As the bogus connection requests come faster than the time out period, the system resources are not freed soon enough. Slowly, all system resources get busy leaving no room for new connections.
2) Ping Flooding
Theoretically, all messages that require a response from the server can be used in a denial of service attack. The idea is to force the server system to spend more and more time trying to respond to requests till it can respond no more.
The ping message, a relatively harmless ICMP echo request, can be used as a powerful tool during an attack. A relative of thePing flooding technique called the Ping of Death used to send very large ping packets that made vulnerable system crash.
3) UDP Flooding
The UDP protocol does not have any flow control mechanism, connection state tracking or datagram sequence numbers. Unlike the TCP, the UDP protocol does not maintain a tab on the expected packets.
It is therefore extremely easy to flood the UDP ports so that the server becomes too busy responding to packets and is left with no resources or bandwidth for network connections.
4) ICMP Redirect Floods
The ICMP redirect message type 5 is used to update the routing tables to acknowledge a shorter route. A server that acknowledges redirect messages can be attacked by sending wrong information in the packet. This could make the server send all traffic to the attacker’s computer thinking that it is forwarding traffic to another remote host.
5) Other Types of Denial of Service Attacks
Apart from the network connectivity, a server system can come under attack through other methods such as file system overflow etc.
Some of the most common methods known to have been used in denial of service attacks are:
a) File System Overflow
If a server system has to write messages in the error logs or the system is being flooded by large email messages, there is a risk of the file system to overflow.
b) Buffer Overflow
When large amount of data is sent to the server, the input buffers of the server can overflow resulting in a system crash.
c) Network Services
Invoking a service such as the network service repeatedly can rapidly exhaust the system memory, CPU cycles and other important system resources.
What is Distributed Denial of Service Attacks
A denial of service attack can occur from a single computer or from a network of computers. When the attack is planned and designed from a distributed network system, it is known as Distributed Denial of Service Attacks.
While it is possible to bring down a server of a smaller website using any of the denial of service techniques, it is not so easy to bring down the server of larger websites. This is because larger websites use multiple servers to host their system and use more complicated and secure protocols.
To attack larger websites, a distributed setup is used by attackers who use several machines to target a single website. These machines could be a part of their network or could be ones infected with a virus. These viruses, known as bots, are malicious programs that are targeted to bring down a particular website. With hundreds and sometimes thousands of systems flooding the website server with requests bring the server to a point where all its resources are exhausted and it can no longer respond to new ones.
Layer 7 DDOS
All the techniques used in denial of service attacks are also used in a distributed denial of service attack. A more direct and brutal technique is the Layer 7 Denial method that can bring down any website within a very short time.
In the Layer 7 Denial of Service attack, the webserver application is the target. Therefore, instead of sending too many requests, the focus of the attack is centered on the webserver application. False requests are sent to the webserver application but are not completed making the server go into a state of waiting. Very few such requests are enough to make a website unresponsive and crash.
7 Ways to Save Your Website from DOS and DDOS
It is quite impossible to stop a denial of service attack of any kind. The best thing that anyone can do is to make it harder and try to take all steps necessary to prevent an attack from occurring.
While you may want to focus on who could be attacking your website, it may not be possible to guess that correctly. Potentially anyone can be an attacker and bring your server down. Instead, it is better to focus on what you have to protect.
1) Setting up a Filter
A filter can sift through information before it reaches the web server. It can analyze the information. This will enable it to determine genuine messages from bogus ones and stop any attacks from happening.
2) Installing Firewalls
Similar to a filter, all messages to the server have to pass through the firewall. A firewall can be configured to allow or reject requests accordingly.
3) Server Configuration
A server can be configured to prevent situations that can result in all its resources getting consumed.
a) You must limit the services that your server can run at a time. This could be the number of different services or the number of instances of the same service.
b) All network ports that are not in use must be closed.
c) Restrict access according to the IP addresses.
d) Create separate partitions for error messages and emails so that they do not jam your system.
4) Disable UDP Ports
As TCP protocol is a more secure protocol, it is best to use TCP and not UDP services if that is possible. Disable all inherently insecure UDP services and UDP ports.
5) Deny Ping Requests
As ping command can be and has been used in denial of service attacks, you may consider limiting the acceptance of ping from remote hosts. Best method is to reject all external ping requests altogether to cut down the risk of attacks.
6) System Updates
Software companies constantly research and release updates for their products & services to make them more secure or add features for better management. Ensure that the software you use is updated as per the official releases from the company.
7) Antivirus
Individual computer users must ensure that their systems are not prone to virus attacks so that they do not become a part of a distributed denial of service attack unknowingly. Ensure that an antivirus is installed and updated on a regular basis.
Conclusion
Though you may have taken every precaution, there is still a chance that your server can get attacked. As attackers are extremely clever people with sadly malicious intent, it is quite difficult to stop them from finding loopholes in the system and using them to their advantage.
However, a question that arises here is ‘why is there little that is done post a denial or service attack?’. You hardly see anyone being caught, or sentenced for such an attack which is nothing less than a crime.
Cyber laws are way behind on this and there is little that the cyber police can do to catch them. Most of the attackers actually do not consider themselves as attackers or hackers and think of themselves more as “hacktivists”.
They like to prove a point, and they do it by bringing down big websites on their knees. And yet, the point that they want to prove is seldom clear.
Other questions that arise here are:
- Since denial of service attacks have been around forever, why can’t they be stopped?
- Are the protocols designed weak?
- Is it necessary to re-design and re-write some of the most basic of protocols to plug the loopholes?
None of these questions have an easy answer. For now, as the owner of a business, you have to take the onus of protecting what you have. Employ elaborate defense strategies to set up barricades and stop denial of service attacks aimed to bring you down.
Has your website ever experienced denial of service attacks? Do you know of someone whose website went through the ordeal of denial of service attacks? Write your opinions and share your thoughts and experiences. Let us endeavor to build a better web world.









I have heard of this happening actually learned about it back in the late 90’s early 00’s haven’t really paid DDOS attacks any attention since then. Thanks for a good recap on it.